Apple PCC Explained: How Apple Redefines Cloud Security
How the World's Most Valuable Company Designed Its Most Secure Cloud
Hey folks welcome back, a few months before their annual event WWDC 2024 where they present new products, Apple released a detailed blog post explaining how they approach security and privacy in this AI-driven, personal data-consuming age. I have to admit that I’m really impressed with Apple’s effort. Though I’m not an Apple fanboy, as my friends know, the work they did here is impressive. It covers all layers of the OSI model and more, ensuring that the supply chain is involved in security control processes. Let’s analyse together.
Private Cloud Compute (PCC) Objectives
Apple’s effort to design and build a Secure Private Cloud Computing environment has been driven by the desire to:
Provide personal intelligence system that brings powerful generative models to iPhone, iPad, and Mac in a secure and private way
Guarantees data is processed without being stored.
Ensures personal data security in AI and cloud services.
What Does “Secure” Mean?
Before to proceed, we should ask ourselves how we define the concept of security and privacy in this context?
As the famous quote says
The only truly secure computer is one buried in concrete, with the power turned off and the network cable cut
Security is always a compromise between safety and usability, and like everything in computer science and in life, there is a trade-off to make between cost and benefit of a new capability.
Let’s explore how Apple defines "secure" in the context of their Private Cloud Compute (PCC) design, focusing on generative AI features:
Stateless computation: When using features like personalized Siri or on-device machine learning, Apple wants to process your data without storing it.
Enforceable guarantees: This essentially means Apple is reducing the use of external components that are not part of their dedicated infrastructure to maintain control over security and privacy. By doing so, they avoid potential risks that arise from relying on third-party systems. They are also reducing the functionality of each component to the bare minimum needed, like in the example of the monitor and logs, where Apple ensures that necessary functions like server metrics and error logs are collected in ways that do not compromise privacy. This means they are carefully selecting both internal and external components while maintaining essential functionality without weakening privacy guarantees.
No privileged access: Whether you’re interacting with an AI assistant or using recommendations, Apple staff have no access to your data—even in emergencies.
Non-targetability: Apple’s approach to non-targetability in PCC means they ensure that users cannot be uniquely singled out or targeted based on their data. This reduces the risk of attacks or data leaks focusing on specific individuals. By designing systems that do not retain identifiable user data or expose unique information, Apple makes it significantly harder for attackers to isolate or trace individual users. Essentially, the system processes user data in a way that prevents malicious actors from identifying or exploiting specific user profiles for targeted attacks.
Verifiable transparency: Apple ensures that users and independent auditors can verify the privacy and security measures within PCC. By providing system logs, publishing software, and implementing open processes, Apple allows third parties to independently confirm that the privacy claims they make are accurate. This transparency builds trust by letting users and auditors see exactly how their data is being handled, ensuring that the system operates as Apple promises without hidden risks or privacy compromises.
Now that we have a clearer understanding of the WHAT (Apple's security and privacy goals) and HOW (the technical mechanisms like stateless computation, non-targetability, and verifiable transparency) let's explore the cloud architecture designed by our friends in Cupertino.
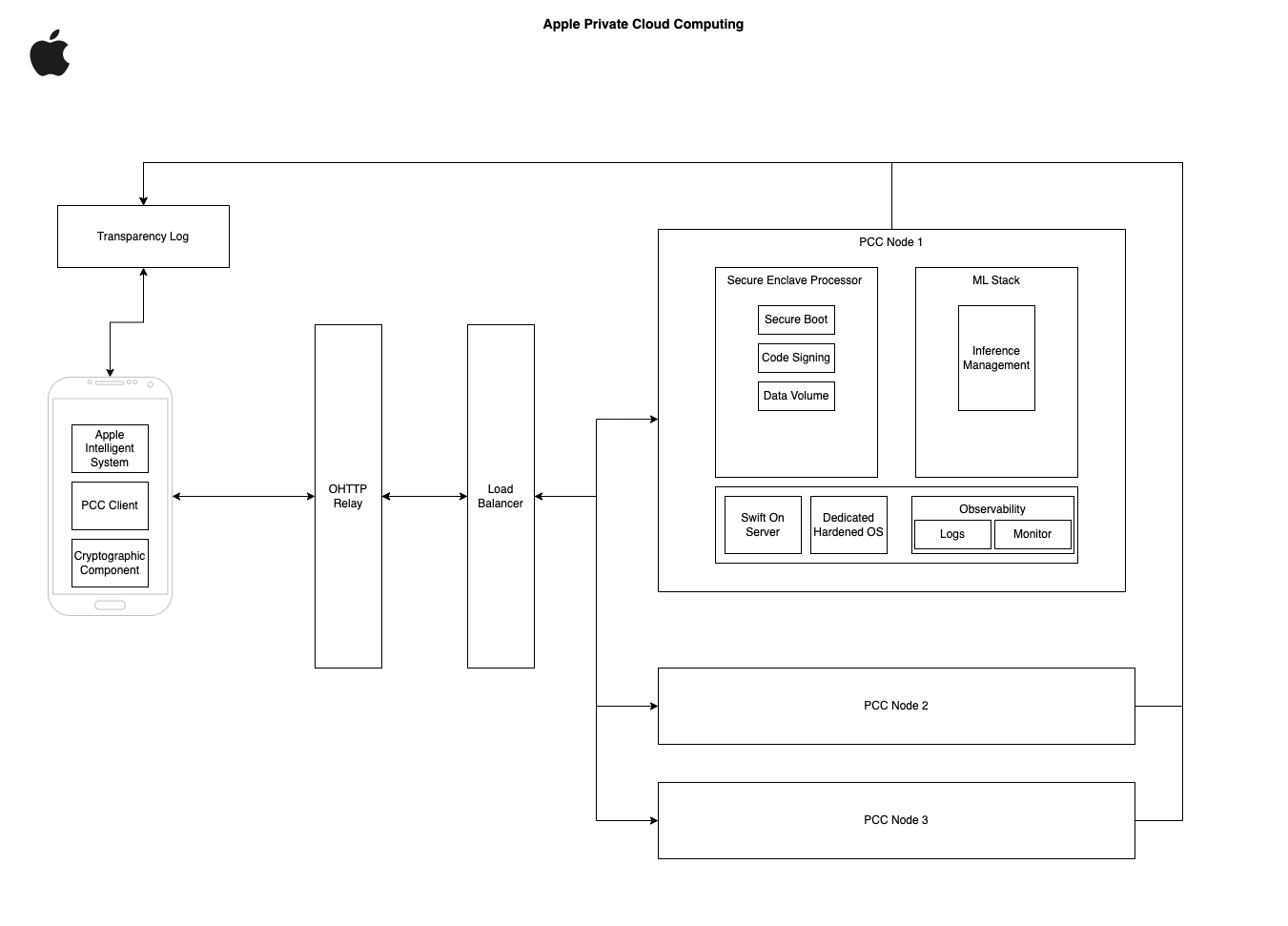
Context Diagram
Apple's Private Cloud Computing (PCC) architecture represents a paradigm shift in secure, privacy-preserving cloud AI processing. Let's analyze each component:
User Device:
Apple Intelligence System: Serves as the frontend for advanced AI features, interfacing between user interactions and the PCC backend.
PCC Client: Crucial for secure communication with PCC infrastructure. Implements end-to-end encryption and certificate verification against the Transparency Log.
Cryptographic Component: Manages key generation, encryption, and signature verification. Critical for maintaining the security boundary between device and cloud.
Implements IP address anonymization, a key element of the Target Diffusion strategy.
Decouples user identity from requests, enhancing privacy at the network level.
Expand on this HERE
Load Balancer:
Distributes requests across PCC Nodes without bias, supporting the non-targetability requirement.
Implements part of the Target Diffusion strategy by selecting nodes without user-specific information.
PCC Node:
Secure Enclave Processor: The cornerstone of PCC's security model. Manages secure boot, code signing, and cryptographic operations. Its hardware-based root of trust is pivotal for the system's integrity.
ML Stack: Handles inference processing. The separation from the Secure Enclave represents a clear delineation of concerns between security and processing tasks.
Swift on Server: Enables custom cloud extensions, providing a balance between performance and memory safety.
Dedicated Hardened OS: Incorporates advanced security features like sandboxing and pointer authentication codes. This bespoke OS is crucial for maintaining a minimal attack surface.
Data Volume: Managed by the Secure Enclave, ensuring data remains encrypted at rest and is ephemeral between requests.
Observability: Limited to predetermined, privacy-preserving metrics and logs, balancing operational needs with privacy requirements.
Transparency Log:
A public, append-only log that enables verifiable transparency.
Interacts with both user devices and PCC Nodes, facilitating trust without centralized authority. Critical for the system's auditability and for enabling third-party verification of PCC's security claims.
Architectural Principles:
1. Stateless Computation: The architecture ensures that user data is processed transiently, leaving no persistent trace on PCC Nodes.
2. Enforceable Guarantees: Hardware-based security measures and the hardened OS create multiple layers of enforceable security boundaries.
3. Non-Privileged Access: The absence of traditional admin interfaces like SSH significantly reduces the attack surface.
4. Non-Targetability: Implemented through various mechanisms including the OHTTP Relay, Load Balancer behavior, and Target Diffusion strategy.
5. Verifiable Transparency: The Transparency Log enables unprecedented levels of auditability for a cloud AI system.
How the information flow?
Now, I believe that to understand Apple's perspective on security it's important to see how the information travel around the different actors. Let's examine how information flows from a device to the cloud and back. For this purpose, I've created three different sequence diagrams that represent three critical parts of the process:
High-level view of the information sequence flow:
This diagram provides an overview of the entire process, showing the main components and their interactions at a glance. It illustrates the journey of data from the user's device to Apple's Private Cloud Compute (PCC) and back, highlighting the key steps without delving into technical details.
User initiates the request on their device.
The device (which includes Apple Intelligence and PCC Client) constructs and encrypts the request.
The encrypted request is sent to the cloud (which includes Supporting Services and PCC Nodes).
A note indicates end-to-end encryption between the device and cloud.
The cloud processes the request.
The cloud sends an encrypted response back to the device.
The device decrypts the response.
The result is presented to the user.
The cloud deletes the user data after processing.
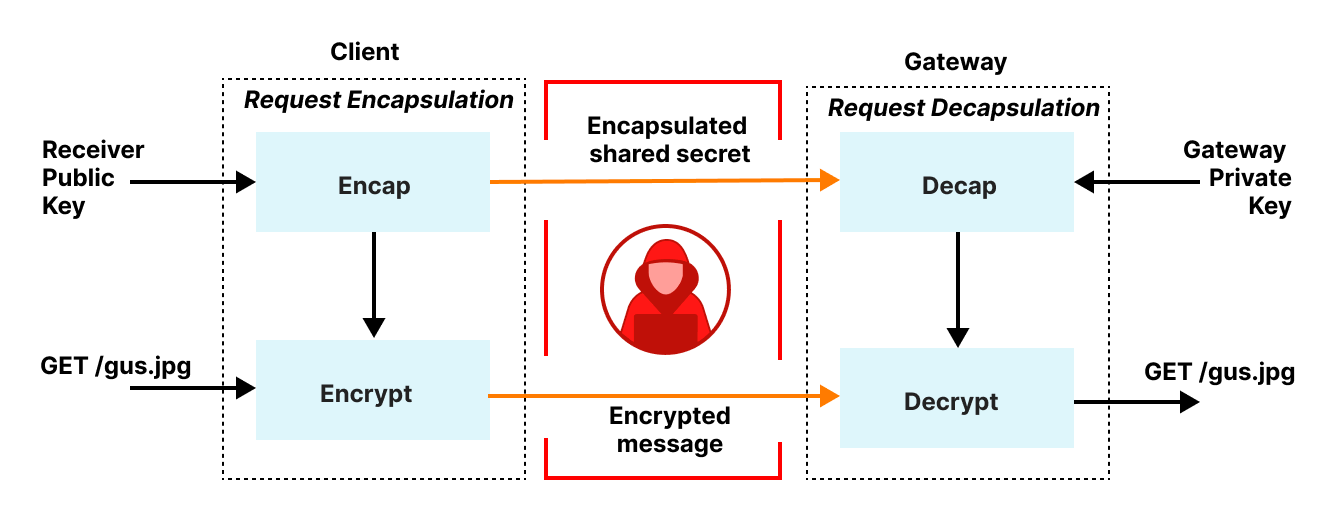
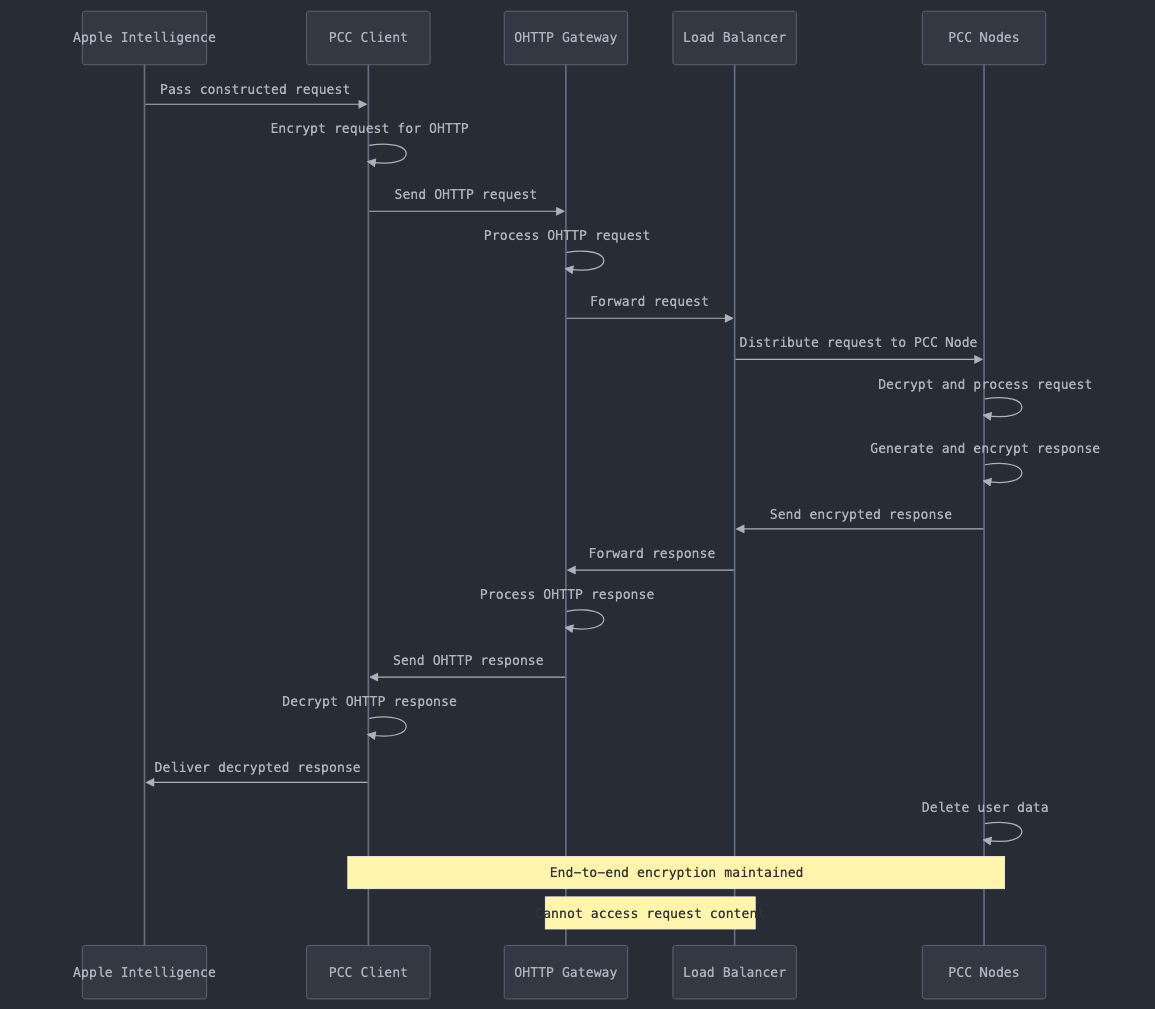
Detailed view of the information sequence between the device and the PCC:
This diagram zooms in on the interactions between the user's device and the PCC system. It showcases the specific steps involved in securing and transmitting data, including encryption processes, the role of intermediary services like OHTTP and load balancers, and how end-to-end encryption is maintained throughout the communication.
Initial Request Handling:
Apple Intelligence passes the constructed request to the PCC Client.
PCC Client encrypts the request for OHTTP transmission.
OHTTP Gateway:
The encrypted request is sent to the OHTTP Gateway.
OHTTP Gateway processes the request, providing an additional layer of privacy.
Load Balancer:
OHTTP Gateway forwards the request to the Load Balancer.
Load Balancer distributes the request among PCC Nodes.
PCC Nodes:
PCC Nodes decrypt and process the request.
They generate and encrypt the response.
Response Path:
The encrypted response is sent back through the Load Balancer and OHTTP Gateway.
PCC Client decrypts the OHTTP response.
The decrypted response is delivered to Apple Intelligence.
Data Deletion:
PCC Nodes delete the user data after processing.
Security Notes:
End-to-end encryption is maintained throughout the process.
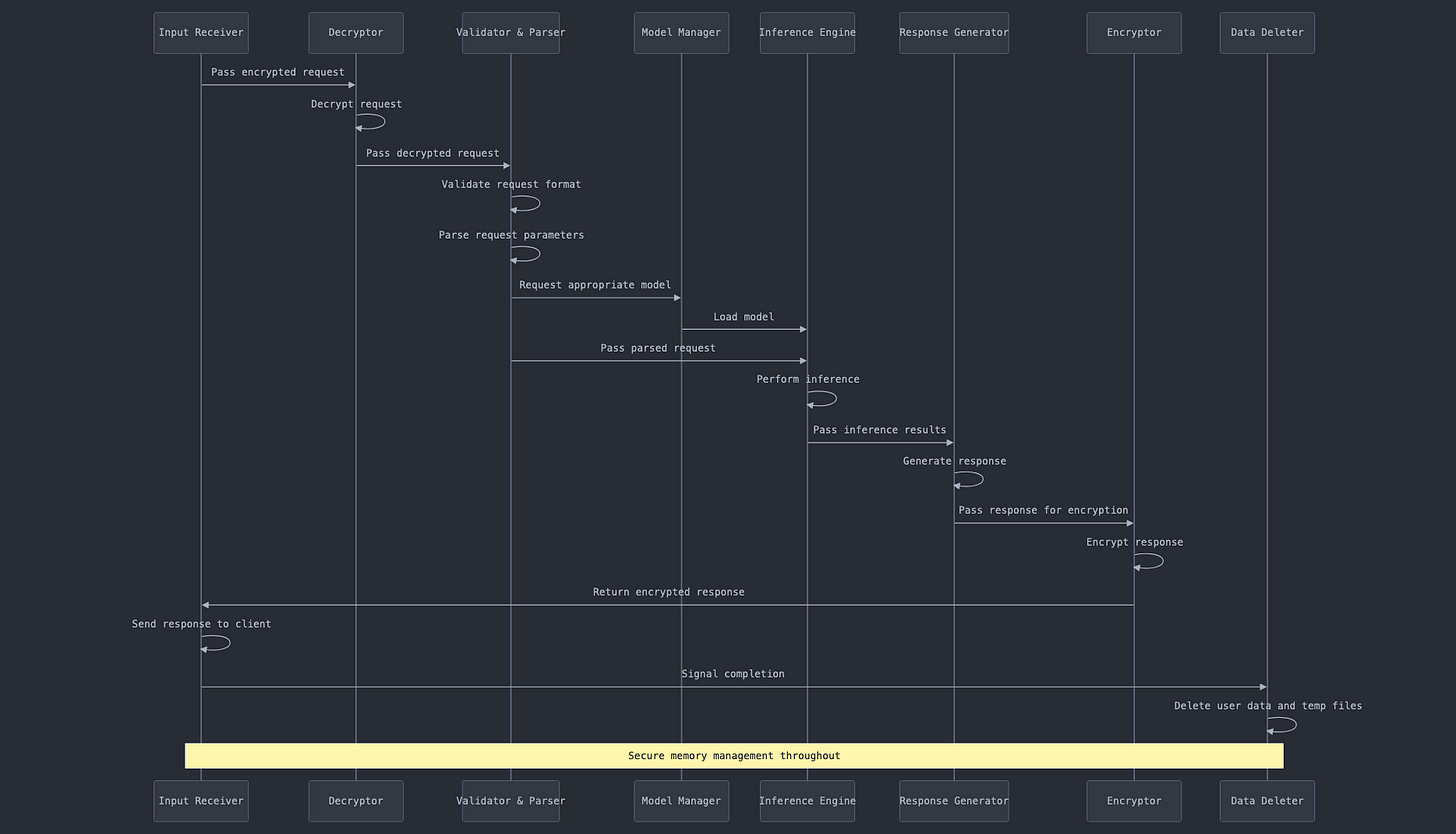
Information flow inside the PCC:
The final diagram focuses on the internal workings of a PCC node. It illustrates how data is processed within the secure environment, including steps like decryption, validation, model inference, response generation, and the crucial process of data deletion after use. This diagram emphasizes the security measures and ephemeral nature of data handling within the PCC.
Input Reception:
The Input Receiver gets the encrypted request from the network.
Decryption:
The Decryptor decrypts the received request.
Validation and Parsing:
The Validator & Parser checks the request format and parses the parameters.
Model Management:
The Model Manager is asked to provide the appropriate model for the request.
Inference:
The Inference Engine loads the model and performs the inference based on the request.
Response Generation:
The Response Generator creates a response based on the inference results.
Encryption:
The Encryptor encrypts the generated response.
Output:
The encrypted response is sent back to the client through the Input Receiver.
Data Deletion:
After completion, the Data Deleter removes all user data and temporary files.
Security Note:
A note emphasizes that secure memory management is maintained throughout the process.
These three diagrams, when viewed together, provide a good understanding of Apple's approach to securing user data in cloud-based AI processing. They highlight the multiple layers of security and privacy measures implemented at every stage of the data's journey, from the user's device through the cloud infrastructure and back.
Beyond Software and Network Security
Apple's commitment to security in their Private Cloud Compute (PCC) system extends far beyond software measures, reaching deep into the hardware supply chain. Their approach to hardware security is exemplary and comprehensive, beginning at the manufacturing stage and continuing through to deployment in data centers.
The process starts with meticulous inventory and high-resolution imaging of each PCC node component. This detailed documentation occurs before the server is sealed and its tamper-evident switch is activated, creating a verifiable record of the original state of each unit.
Upon arrival at the data center, these servers undergo an extensive revalidation process. This crucial step involves multiple Apple teams working independently to cross-check data from various sources, ensuring the integrity of each unit. To further enhance transparency and trust, this process is monitored by an independent third-party observer with no affiliation to Apple.
The culmination of this rigorous process is the issuance of a unique certificate for each PCC node. These certificates are cryptographically rooted in the Secure Enclave's Unique Identifier (UID), providing an unbreakable link between the physical hardware and its digital identity.
Apple's security model extends this trust to the user's device. The system is designed so that a user's device will refuse to transmit data to any PCC node whose certificate it cannot validate. This creates an end-to-end chain of trust from the manufacturing process all the way to the user's interaction with the PCC system.
These measures demonstrate Apple's holistic approach to security, protecting the hardware from potential compromises at every stage of its lifecycle. By implementing such thorough and transparent processes, Apple has set a new standard in hardware security for cloud computing infrastructure.




Hi,
I hope this message finds you well.
My name is Aditya,I have been working as an SEO Manager for the past 8 years.
I recently came across your website and was impressed by its design and content. However, I noticed that its ranking on search engines like Google, Yahoo, and Bing could be improved.
If you're interested, I would be happy to share our SEO packages details with you.
Please let me
know
Thank you for your time!
Best regards,
Aditya